Cyber Risk Review
Model, optimize and control your response to cyber risks.
Improve your cyber resilience with our defense optimization model and optimal operational and executive management.
Functionalities
-
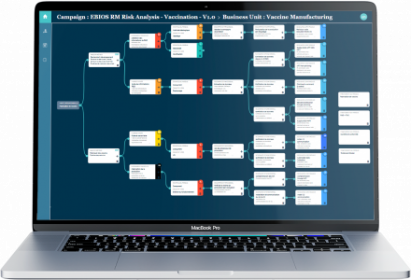
Model cyber attacks
 Homogenize, standardize and reduce risk analysis bias
Homogenize, standardize and reduce risk analysis bias -
Optimize your defenses
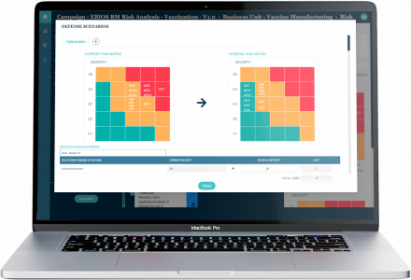 Have a cyber risk treatment plan tailored to your needs, ensuring the best ROI and an optimized TCO
Have a cyber risk treatment plan tailored to your needs, ensuring the best ROI and an optimized TCO
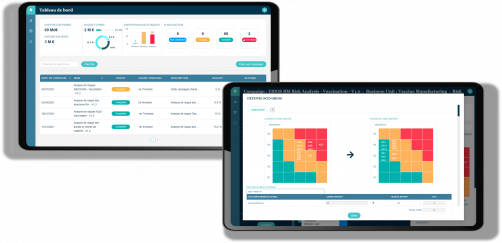
Master your cyber threats

Improve your cyber resilience with our defense optimization model and optimal operational and executive management.
-
Master your cyber threats
The evolution of the risk surface continuously
The status of your exposure to various regulatory sanctions
Tracking of consumed and forecasted risk treatment budgets
The distribution of budgets within the different departments/locations/business lines
Progress of action plans -
Model cyber attacks
Choose the appropriate cybersecurity risk analysis framework from the best standards on the market (EBIOS RM and NIST) that meets the ISO27005 standard.
Benefit from an intuitive user experience tailored to cybersecurity operational staff and risk owners for efficient operational management and top management for executive reporting purposes.
Have an enriched and continuously updated catalog of cyberattacks based on the work of the MITRE® organization and Lockheed Martin.
Calculate your residual risk based on comprehensive and continuously updated defense frameworks based on CIS Controls, NIST CF, and MITRE D3FEND®.
Quantify the benefits of each defense measure, weighted by its nature and effectiveness.
Diagram all possible cyber attack scenarios detailed by phase
-
Optimize your defenses
Select your target cyber risks and let the tool optimize them with minimal effort.
Reduce your cyber risks by strengthening the defenses associated with the most feared attack scenarios.
Simulate several cyber risk treatment plans according to your different operational, financial, and regulatory criteria and select the one that best suits your needs.
Effectively justify your needs, objectives, and alignment with your budget through intuitive and dynamic dashboards.







